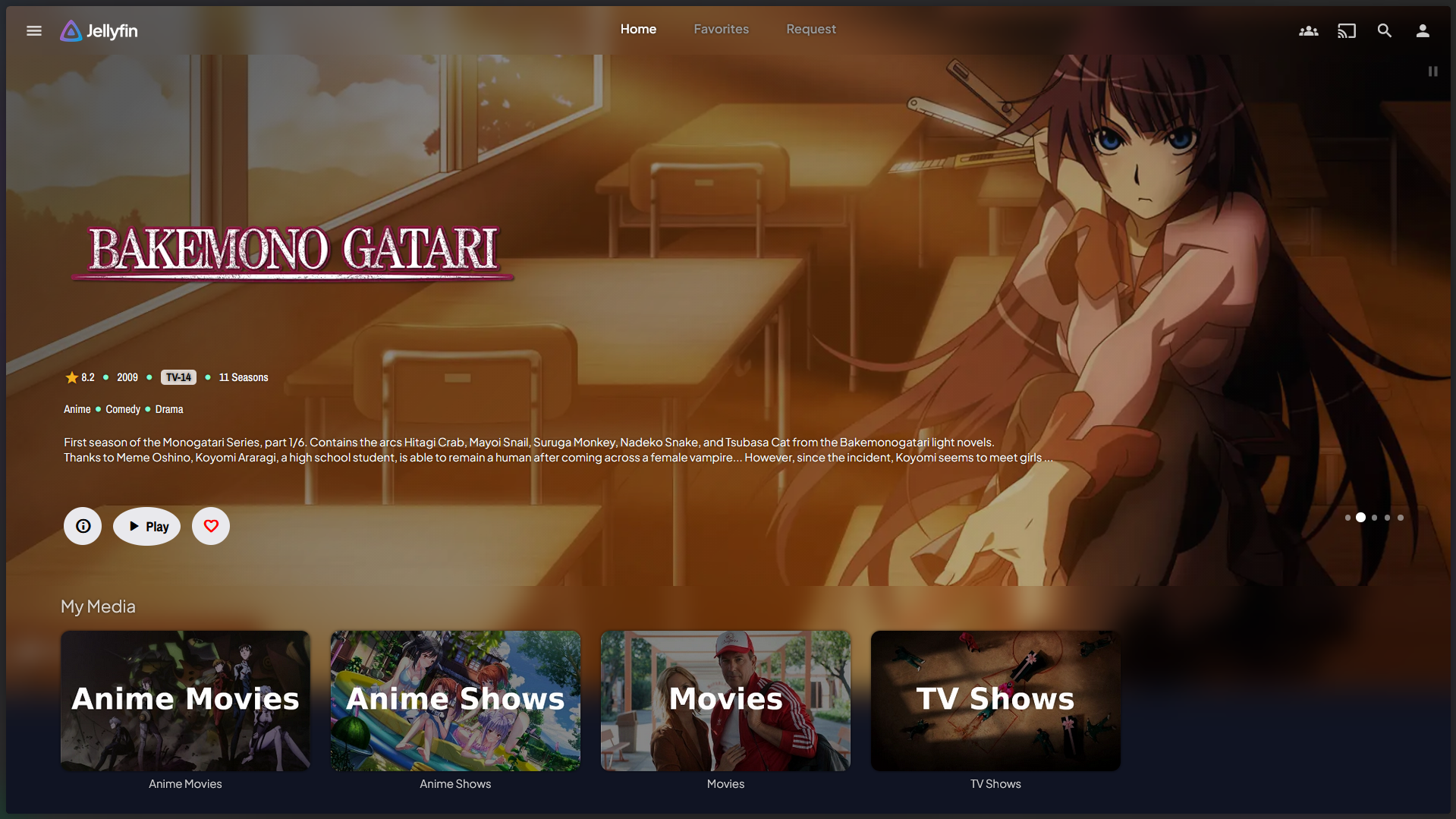
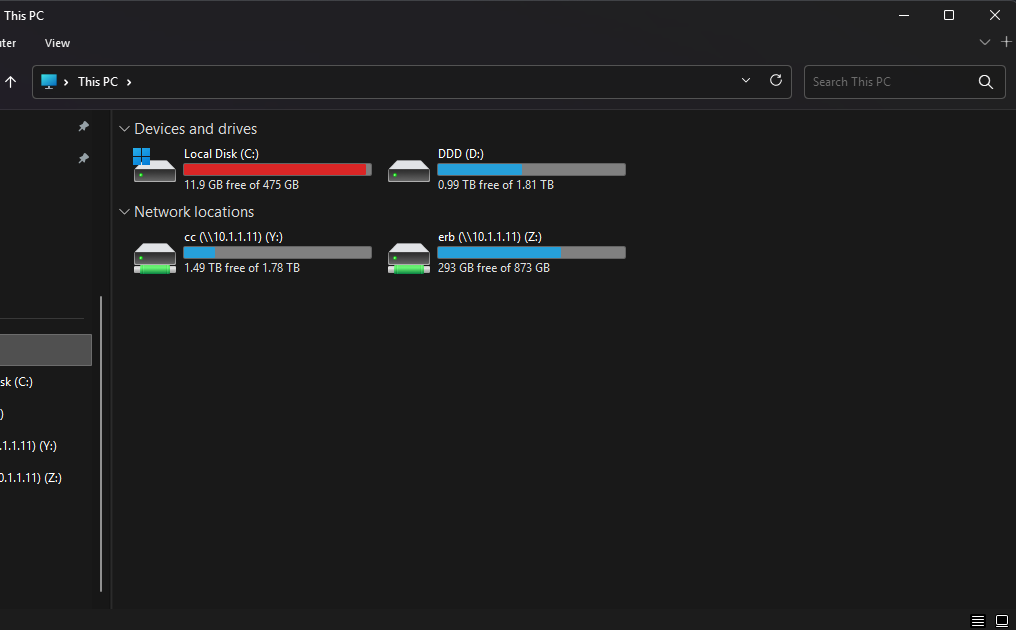
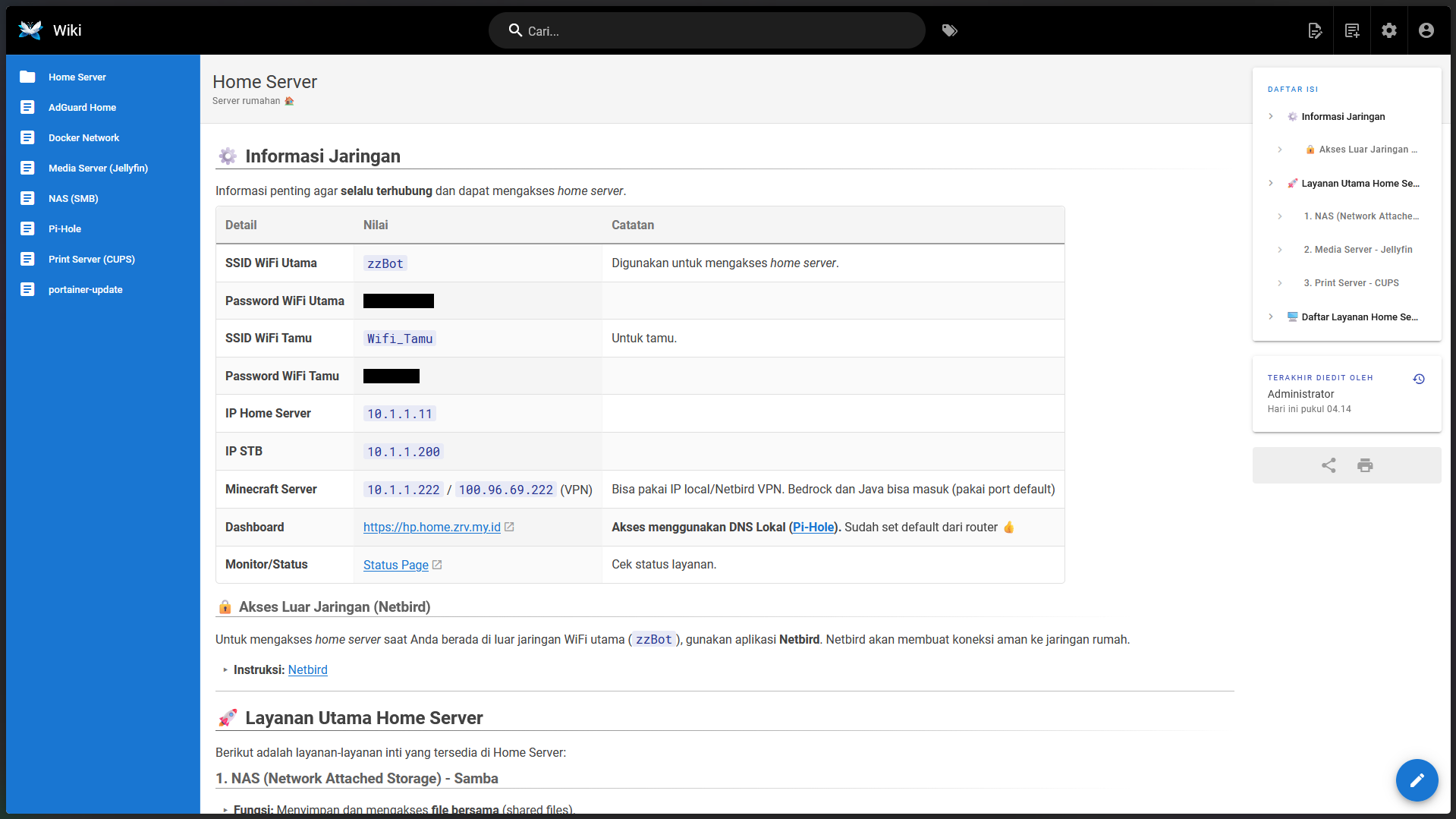
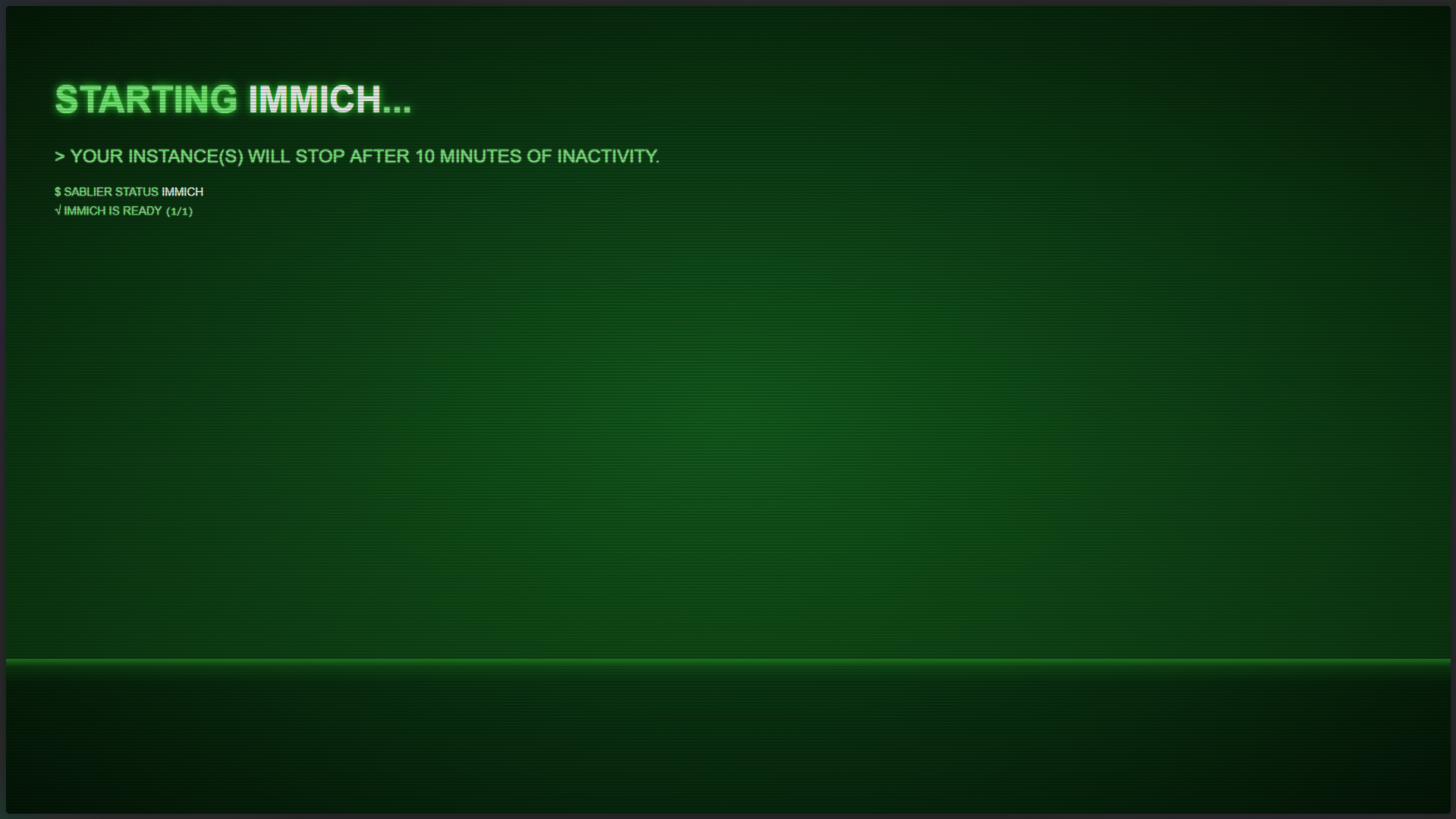
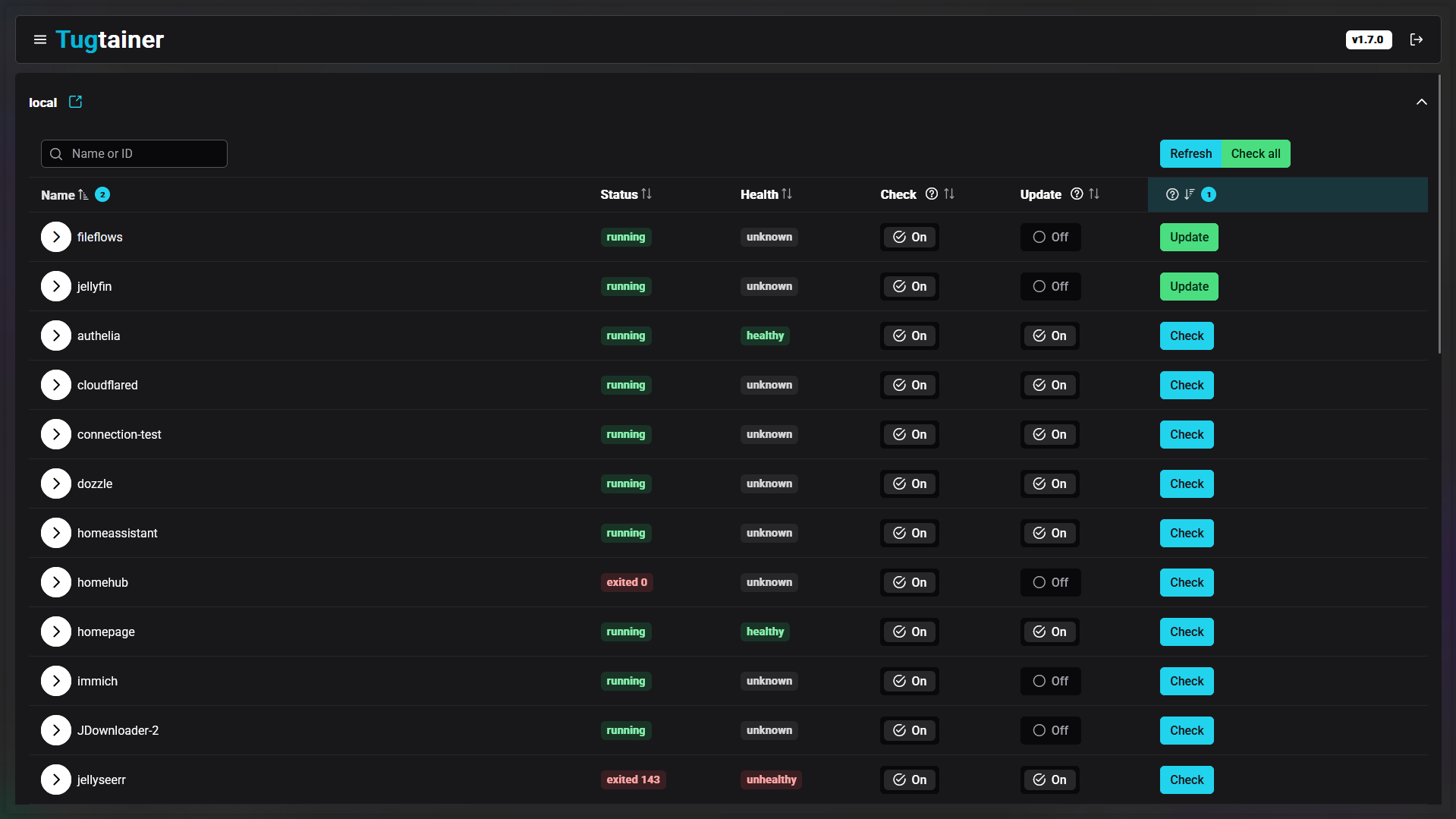
I’m proud to present my Home Server: “Project Second Wind.” This infrastructure was designed with a philosophy of prioritizing robust services over premium hardware, leveraging a decommissioned laptop and a Set-Top-Box (STB) to build a complete and powerful self-hosted ecosystem.
This setup is proof that complex infrastructure solutions can be achieved with resource-efficient hardware and a sharp focus on software optimization.
💡 Resource-Efficient Architecture #
A visual look at this intelligent hardware architecture, built from upcycled components yet engineered for 24/7 reliability.

I intelligently split the workload across two distinct devices to maximize limited hardware capabilities:
| Key Device | Core Specification | Primary Role |
|---|---|---|
| Main Server (Asus X540MA) | Intel N4000, 4GB RAM, Debian 12 | Hosting Media, NAS, Automation, and Security/SSO (heavy workload). |
| Edge Compute Node (STB HG680P) | ARM Cortex-A53, 2GB RAM, Armbian | Always-On & Lightweight Tasks: Pi-hole (DNS), CUPS (Print Server). |
🚀 Core Services Stack (Enterprise Functionality) #
Despite the minimal hardware, my software stack is sophisticated and integrated, with all primary services running as Docker Containers on the Main Server.
1. Zero-Trust Access & Security #
-
Reverse Proxy & Edge Security: Traefik + Authelia (Single Sign-On / SSO) fronting Portainer, ensuring all internal service access requires secure authentication.
-
Remote Access: Netbrid VPN and Cloudflare Tunnel (as a fallback or for public service access) for secure remote connectivity.
2. Media & Data Ecosystem #
-
Media Server: Jellyfin (Direct Play Focused, with minimal/non-GPU Transcoding). This setup forces Direct Play on client devices to conserve the limited N4000 CPU resources.
-
Jellyseerr & Wizarr: Automating user requests and family member onboarding.
-
Jellystat: Real-time monitoring of usage and activity statistics.
-
-
Storage: NAS (Samba) mounted to 1TB and 2TB HDDs for data reliability.
-
Personal Photos: Immich (Self-hosted Google Photos) – Data is stored privately, intentionally without heavy-ML processing to reduce CPU strain.
3. Automation & Workflow Efficiency #
Despite hardware limitations, my dashboard displays intelligent service orchestration and automation, ensuring everything runs efficiently.
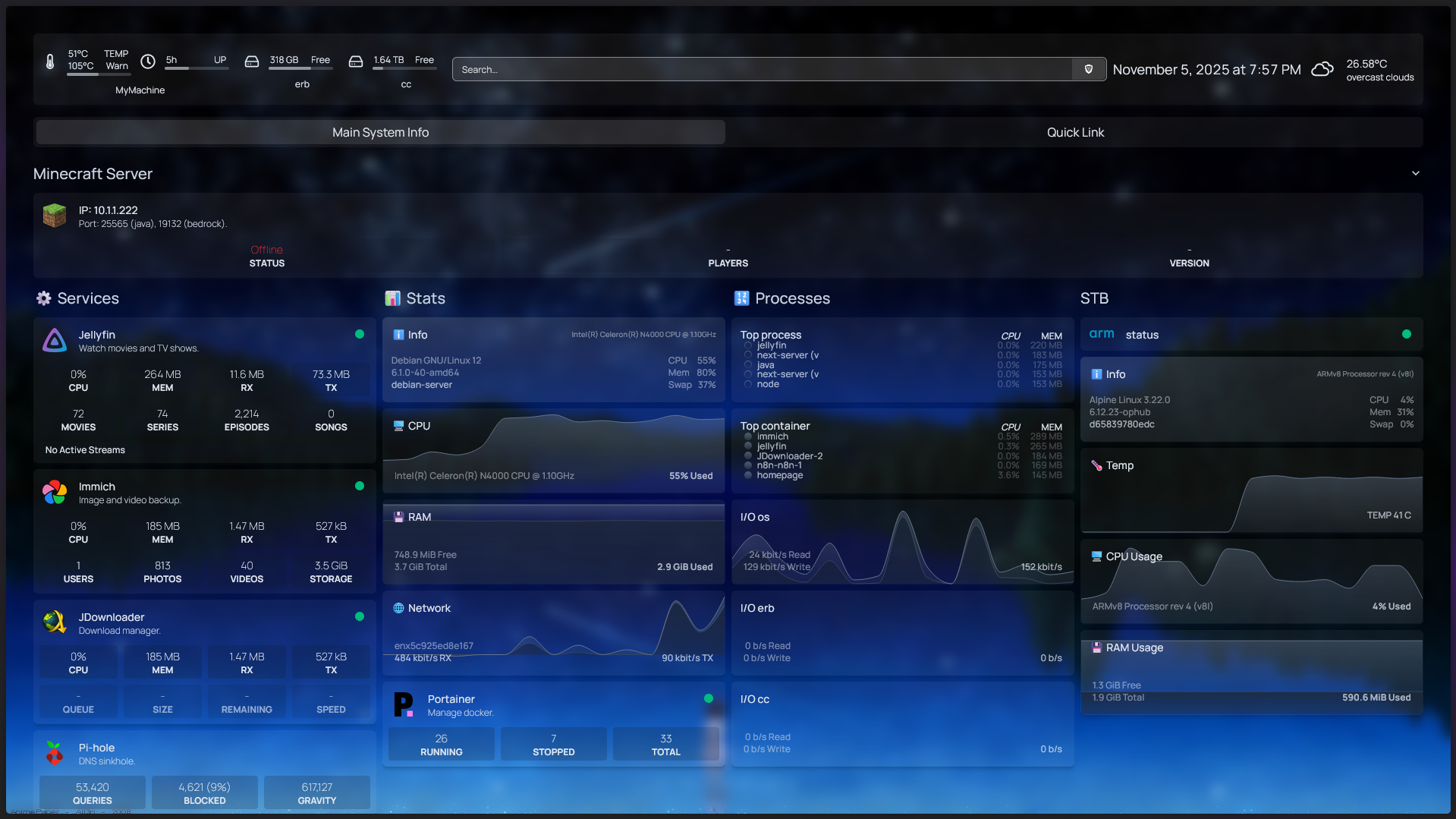
-
Workflow Engine: n8n is used to automate several processes: auto-downloading content, system health notifications, and simple data workflows.
-
Intelligent Transcoding: Fileflows is configured for automated video codec conversion (on-the-fly / scheduled) to H.265, significantly conserving valuable storage space.
-
Demand Loading: Sablier acts as Traefik middleware, shutting down containers (like Jellyseerr/Wizarr) when inactive, drastically reducing the constrained 4GB RAM usage.
4. Stability and Documentation #
-
Monitoring: Glances (CLI), Dozzle (Log Viewer), and Homepage (Dashboard) for real-time visibility into system status.
-
Key Documentation: Wiki.JS – The single source of truth for family user guides and personal troubleshooting documentation.
📊 Implementation Success & Key Learnings #
Below is the Pi-hole dashboard, showcasing the performance metrics and network protection delivered by my dedicated Edge Compute Node.
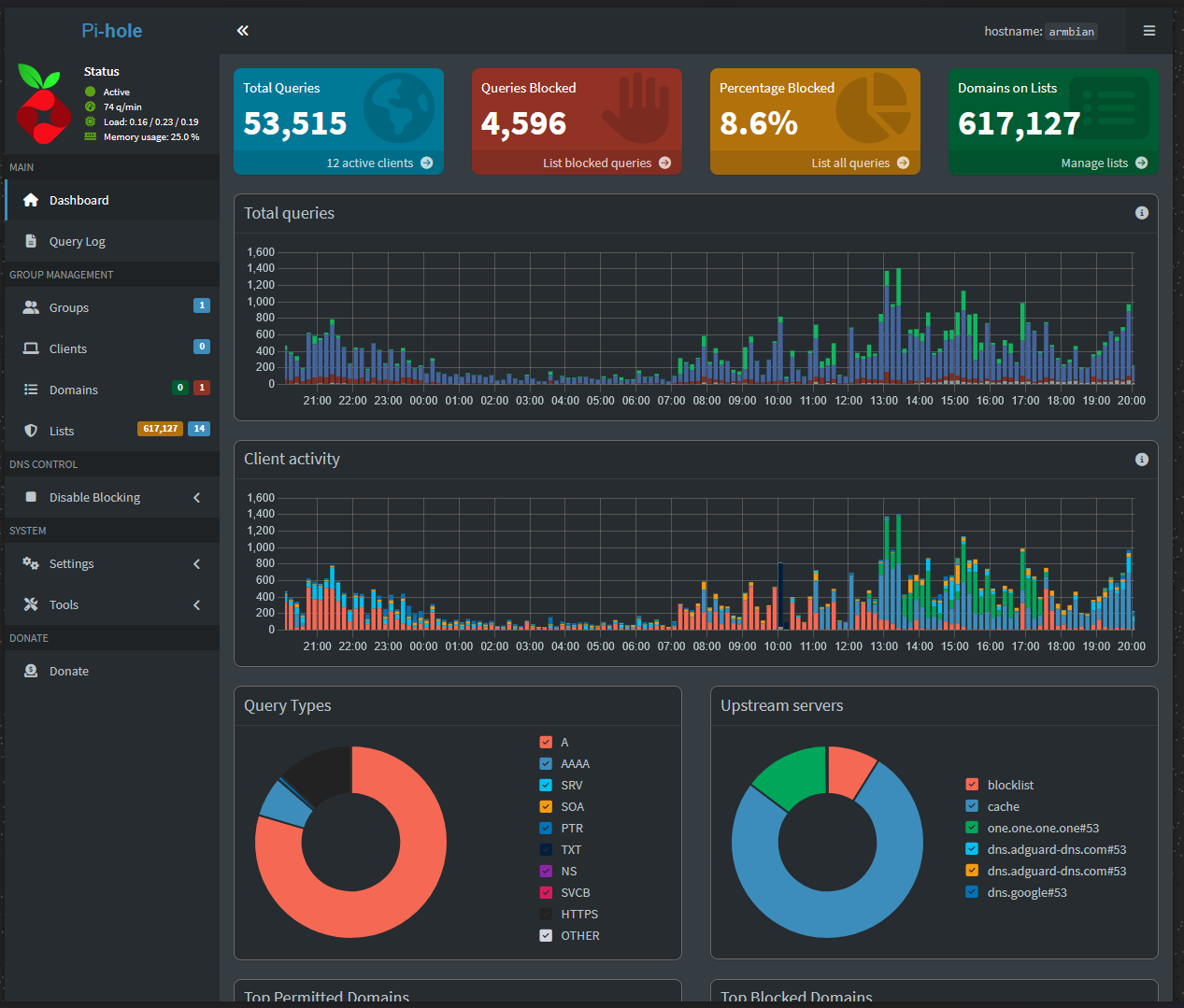
Project Second Wind successfully demonstrates Resource Orchestration excellence:
-
Critical Edge Tasks: Isolating Pi-hole and CUPS to the STB ensures core network services remain stable and independent of the heavier Main Server workload.
-
Software Optimization: The use of Sablier and Fileflows configurations showcases how smart software can directly mitigate severe hardware limitations (the 4GB RAM and N4000 CPU).
-
Layered Security: The combination of Authelia (SSO) and VLANs on an OpenWrt router creates a much stronger security posture than a typical home server.
🔮 Future Milestones (Roadmap) #
This infrastructure is continuously evolving. My next milestones focus on operational security and enhanced High Availability (HA) capabilities:
-
Cybersecurity Hardening (Immediate Focus): 🛡️
-
Secure Authentication: Implementing SSH Key-Only authentication on the Main Server, disabling password-based login to minimize the attack surface.
-
Bruteforce Mitigation: Installing and configuring Fail2Ban to automatically detect and block suspicious login attempts.
-
Geographical Restriction: Utilizing GeoIP Blocking on the Firewall/Edge to restrict access to specific ports from irrelevant geographical locations.
-
-
High Availability (HA) & Orchestration Exploration: 🔄
-
Kubernetes Study: Planning the implementation of lightweight Kubernetes (K3s/K0s) as a learning project to understand container orchestration and HA configuration.
-
HA Goal: Testing failover for critical stateless services (e.g., the Reverse Proxy) within the K8s/Docker environment to improve system uptime.
-
-
Data Backup & Redundancy:
- Off-Site Backup: Adding cron jobs and scripts for backing up critical data (Docker configs, databases, Immich metadata) to an encrypted cloud storage solution.
🖼️ Gallery #